A Comprehensive Deep Dive into Elusiv
Encrypting web3 transactions with gated privacy and decentralised compliance 🔐
As we go into the future, web3 transactions will be the mainstream medium to transfer money and any form of digital value. And this mainstream adoption of payments and transactions would be on chains like Solana, which enable almost instant transaction speeds, with decentralized, secure, and scalable solutions.
But all the public blockchains store this data in a public ledger that can be queried and indexed at any time. This creates a goldmine of publicly available transaction data and as it gets accumulated over time, there will be a massive boom in web3 social graphs to link and analyze the wallets with high-value transactions and eventually will pinpoint a wallet to an identity.
These social graphs and analyses of transactions can be easily queried on on-chain explorers, to understand how easy it is, let us take an example here. Search any public mainnet wallet address on Solana on an explorer-like Bitquery, this allows users to search the historical transaction data of any wallet with specialized filters like inflow, outflow, and list of all the transactions, as follows:

This explorer also allows users to create transaction graphs by adjusting the depth of the graph to interact with all the wallets which are associated with a transaction and its corresponding public wallet, as seen in the above representative image.
Imagine Alice and Bob are neighbors, who purchase their daily essentials from the same supermarket down the lane, with crypto. And as they are neighbors they frequently share crypto with each other for regular transactions, this allows Alice to search for Bob’s supermarket purchase using Bob’s public wallet address, and Bob can do the same with Alice’s wallet address.
This breaks the privacy that web3 is promising to offer, they can create secondary wallets, but with tools like Explorers, one can easily query all the linked secondary wallets by tracing the transfer records!
This is where Elusiv comes in! Elusiv as a platform provides users with:
Encrypted Transactions
Fully Private Transactions
Gated Transactions where you can choose whom to share the transaction details with!
Decentralized compliance (Finally something with no KYC 😌)
Warden Network to protect users from transaction tracing!
And many more such features! These features bring the privacy that web3 users really deserve!
In this Deep Dive, let us start exploring the ins and outs of the technical design of Elusiv, before that let us understand why this technology is ground-breaking in consumer web3!
Privacy: Web2 vs Web3
Both web2 and the current version of web3 constitute their own set of privacy concerns, varying on factors taken into consideration. In this section let us begin with an analysis of the current privacy properties on web2 and web3.
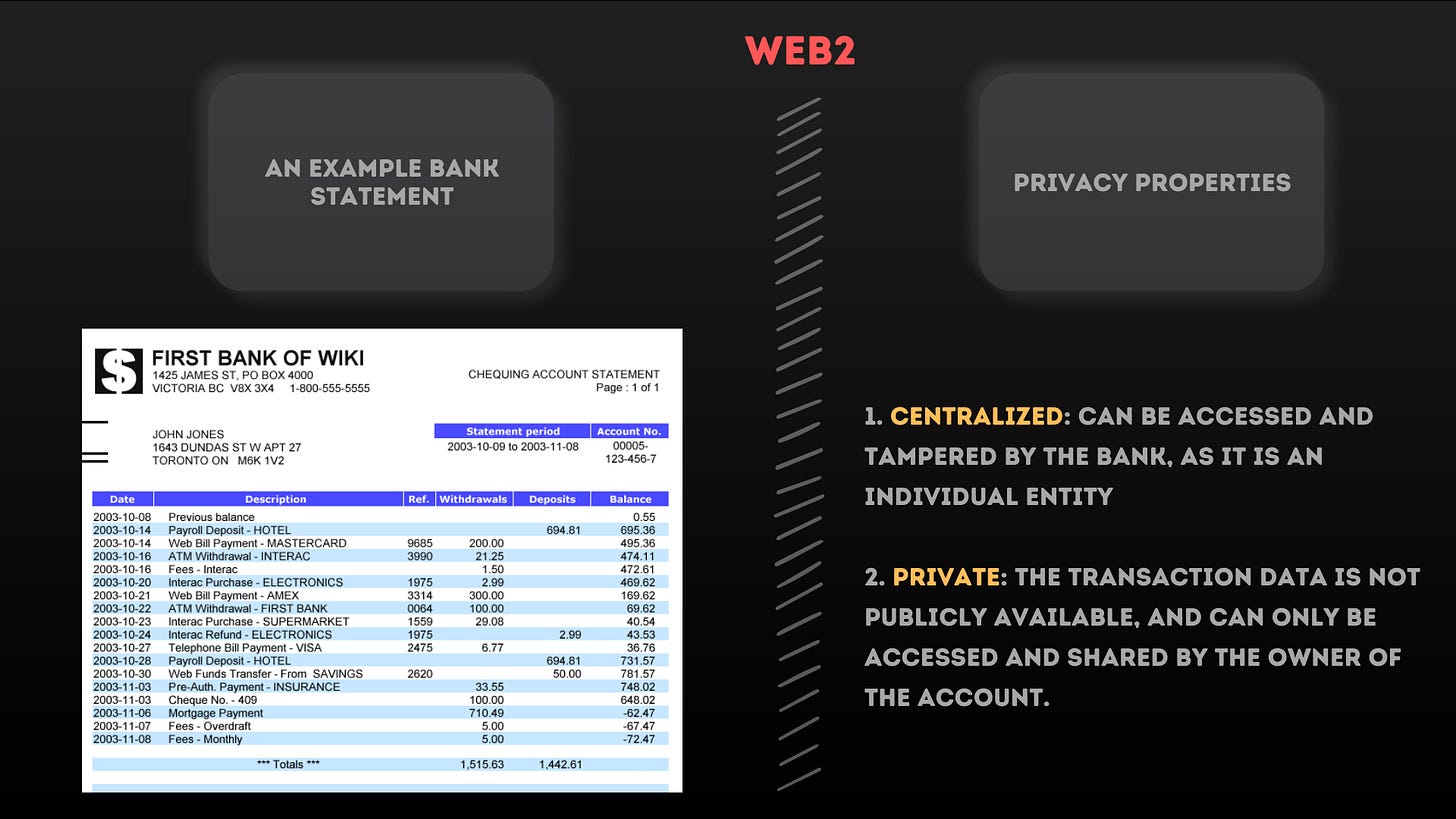
To understand these properties let us take a classic financial example, a Bank statement. A bank statement is a historical collection of financial transactions associated with an account. This is analogous to public wallet transaction data in web3 terms.
In the web2 world, financial transactions go through intermediaries like Banks, to settle funds between the sender and receiver. In our example, when we consider a Bank Statement, it is the collective history of transactions done by the account holder, which include debiting or sending the money or crediting, receiving the money from another account holder.
But the point of discussion regarding this example is around the privacy properties of a Bank statement, and these logs of financial transactions are:
Centralized: Because these transactions can be accessed and have a probability of being tampered with by the central authority that controls the storage of these details, the Bank.
Private: Bank statements are generally private in nature, as they can be accessed only by the account holders and these logs are not readily available for public display, until the account holder decides to share.
These properties conclude a positive and a negative side of web2-based financial transactions. Although they are private and can be only accessed by the account holder, they are under the control of a central authority, thus making them unfavorable compared to what modern blockchain and web3 solutions have to offer.
Coming to the web3 world, Blockchains are analogous to Banks, Wallets are analogous to Accounts, And explorer data as we saw with the Bitquery Explorer, are analogous to a Bank statement. So, when we explore the privacy properties of a web3 public wallet account’s explorer data, they are:
Decentralized: Firstly, the transaction data associated with a web3 public wallet address is decentralized, thus these records are stored on a decentralized network of systems, which constitute the blockchain itself. Thus these records cannot be tampered, with by any single entity, like a bank in the web2 scenario.
Pseudonymous: Blockchain data from public blockchains like Solana, and Ethereum, are inherently pseudonymous, this results in a public view of the transaction logs, but avoids pinpointing the user identity itself. But as we saw in the introduction, with modern explorers, better data mining algorithms, and as more data gets accumulated over time as web3 goes mainstream, this pseudonymity can be overcome by data analyzers leading to an easily predictable user identity linked to a wallet address.
But web3 needs a platform for users to be able to conduct private transactions, to avoid linking these transactions to a user’s identity.
This requires the best of the both web2 and current web3 scenario of transaction record handling, and Elusiv brings us just that!
The above discussion points to the importance of privacy in regard to blockchain transactional data, and how Elusiv is bringing all the following required elements to this mix:
Elusiv is Decentralized: Elusiv does all the transactions on-chain via Solana, thus Elusiv doesn’t compromise on the decentralization that one of the most popular blockchains in the world provides, thus no one including the user can change the historical transaction logs, as they are permanently etched into the blockchain.
Elusiv Transactions are encrypted: All Elusiv transactions are encrypted with ground-breaking cryptography algorithms like ZKP (Zero Knowledge Proofs), and one-of-a-kind ZKP, zkSNARKS (sounds cool right)!
Elusiv Transactions are completely Private and Gated: All Elusiv transactions are private in nature, thus allowing only the sender and receiver to acknowledge the transaction while preventing anyone from tracing the tracks of the transaction to the associated wallets. Elusiv also provides a feature to enable gated privacy, where certain users can view the transaction details, based on the keys generated by the users who perform the transaction!
But, as every field does, there are pioneers in this space, and some spectacular crashes as well. Most of us have learned atomic models in chemistry, right? We went from J.J Thompson’s Plum Pudding model to the advanced Rutherford-Bhor Model of an atom, and there is an important thing to understand here:
“Every Mistake is a stepping stone to success”
So let us see what is one of the biggest mistake done by an early pioneer in this space and how Elusiv is not repeating the same mistake, instead setting the bar high for others to follow!
Lessons Learnt: Understanding the innovation, The Chemistry way!
One of the biggest names which come to a crypto-native’s mind when we discuss Private Transactions on Public Blockchains is: Tornado Cash
It introduced some ground-breaking technology built upon the base set by another amazing name in the field. Zcash’s open-source code. Tornado Cash took the crypto ecosystem by storm and became quite popular in no time! But the way in which it handled the compliance issues early on, lead to a massive breakdown of this decentralized Token mixer by the Federal agencies, which accused this platform of being a base for money laundering and a hideout for other digital crimes.
Tornado Cash is a decentralized, non-custodial, open-sourced Token mixer, to provide anonymity to users who transact with Ethereum or any ERC-20 tokens. This application was built to run on top of the networks supporting the Ethereum Virtual Machine. Tornado Cash provided absolute privacy, encryption and a decentralized transaction environment, similar to the ideal envisions of Elusiv, but they lacked any measures to prevent malicious actors from transacting on their platform with other normal users.
US Department of the Treasury's Office of Foreign Assets Control (OFAC) sanctioned Tornado Cash on August 08, 2022, for giving a chance for cybercrime organizations to transact via the platform and provide digital anonymity to these malicious actors.
Although Tornado Cash is an amazing tool for legitimate users to achieve financial privacy, it can be misused by politicians, hacking organizations and cybercrime blackmails to prevent getting caught by the OFAC and other federal agencies.
These factors allowed the bad actors to money launder approximately 7 billion USD on Tornado Cash since 2019.
So how can future privacy-preserving solutions like Elusiv, prevent bad actors from interacting with Regular users, and prevent any money laundering on a large scale as we saw in the case of Tornado Cash? Elusiv came up with a solution for this called, Decentralized Compliance.
Decentralized Compliance is a set of compliance measures introduced by Elusiv to prevent and allow users to do the following:
Allow users to share the transaction details with absolute control over who can view the details, by assigning a key to each view. This allows them to prove these transactions to the authorities if needed.
A community-driven blocklist to prevent interactions with malicious actors is similar to spam prevention measures taken by Google and telecom companies.
Elusiv also allows users to share just the parts of the transaction that authorities or their associated tax firms need to see, nothing more, nothing less!
As shown in the above image now Elusiv can be called a full-fledged privacy layer on top of the blockchain with encrypted, private, and compliance-ensured privacy layer for the users. From the next section let us deep dive into the core working functionalities of Elusiv!
Elusiv into the act: Privacy Redefined
To sum up the discussion in the previous sections, Elusiv is a platform that envisions a fully private, encrypted, and decentralized layer to perform transactions on top of Blockchains, with end-to-end decentralized compliance for users and authorities to maintain the integrity of the platform. Elusiv wants to redefine the privacy layer of the future web3!
Elusiv was co-founded by 4 young entrepreneurs Yannik Schrade, Nicolas Schaperlere, Lukas Steiner, and Julian Deschler, envisioning to empower the next generation of privacy on Solana. Elusiv also got an honorable mention for their amazing work during the Solana Riptide Hackathon and also got a seed round funding of 3.5 Million Dollars, led by some of the biggest names in the Solana and Crypto industry. Currently, Elusiv runs on top of the Solana blockchain, and the team chose Solana for all the right reasons:
Solana is currently operating at the highest TPS (transactions per second) among all the blockchains out there, with an average mainnet TPS of over 4000, a True TPS of 400, and a practically proven theoretical maximum TPS of over 400k.
Solana operates at a sub-millisecond latency, which is the closest contemporary to the web2 real-time applications while maintaining decentralization.
These factors along with an ever-growing decentralization (Nakamoto coefficient of 34 being one the highest among L1s) and being the only L1 ecosystem with instant to real-time transaction speeds make Solana destined to be a mainstream user-loved ecosystem. And the need for privacy on this amazing chain is more than ever!
In the next section let us get started with the basics of ZKPs (Zero Knowledge Proofs) and zkSNARKS before diving into the intricacies of the technology behind Elusiv!
What are Zero Knowledge Proofs and zkSNARKs
Let us not go into the complex mathematical proofs of Zero Knowledge Proofs yet. Instead, Let us first try to understand this concept using a simple story with our all-time best frens Alice and Bob (yes they are back!) 🥳
Once upon a time in China, there lived Alice a Local Guide, and Bob a Treasure hunter. They both set on an expedition to find an ancient treasure with lots of cold wallets holding hundreds of Bitcoin, sol, and eth (jff 😂), it was holding tons of gold and other valuable items. So after days of failed guidance under Alice, he wanted to know if she really know the location of the treasure that he knows. Or was she trying to mischief him and take the treasure all alone? So they decided to play a game to prove that:
Alice really knew the location of the treasure? or was she wasting Bob’s time??
Also, this needs to be done without Bob or Alice sharing the details about the location of the treasure.
So Bob the verifier who knows the location of the treasure drew a circle around the current location where both Alice and Bob are situated. And he asked Alice to say him the direction to the treasure’s location (it is marked in red, just for the explanation, it was not marked obviously during this experiment, lol !), but with a condition, just say him the route using these four sentences:
Go Straight
Go Left
Go Right
Go Back
This makes sure of three things:
Alice can use these sentences to pinpoint the route from the current location to the treasure.
At the same time, these sentences can mean to go in any direction North, South, East, and West.
The above point in turn ensures that Bob must know the location himself to verify the directions said by Alice.
Thus as Alice makes the route from the current location to the treasure location based on these sentences, Bob finds out that Alice is genuine and she knows the location of the treasure and verifies the same to her.
In this story, the way in which Alice proved that she knew the direction to the treasure to the verifier Bob, without either of them revealing the location they knew, is known as a Zero Knowledge Proof or a ZKP in cryptography.
They are two kinds of ZKPs, zkSNARKs and zkSTARKs. To be precise, both of them are two differenet implementations of the same concept.
zkSNARKS are ZKP implementations without the need for any user interaction.
zkSTARKS are ZKP implementations allowing the users in the scenario to interact.
Elusiv uses zkSNARKS because interactions involve back and forth proof and verification steps to complete the ZKP which makes it really costly to scale to a large number of users. Let us understand the implementation and use of zkSNARKS, in Elusiv’s technical architecture.
Technical Architecture of Elusiv
Let us understand the technical architecture of Elusiv in two different ways:
The Layman Way: Understanding Elusiv Shared Pool 😎
Elusiv uses the concept of a shared pool. A shared pool is basically like a “Mixture” of similar tokens sent by users across the Elusiv platform. From Figure 1 imagine Alice sent 36.5 tokens to the Elusiv pool, and 36.5 tokens went to the receiver in the name of the Elusiv pool, an outsider can easily understand that Alice is the one who sent the tokens, because she is the only one who sent the tokens to the pool.
But what if there are a large number of users contributing to Elusiv’s pool, with different amounts, different withdrawal amounts, and different withdrawal times, the complexity of guessing who sent to whom increases exponentially to a level that it is impossible to determine the sender and receiver’s associated wallet addresses.
The Nerdy Way 🤓
So a simplified technical foundation of the overall Elusiv encryption standard can be broken into three phases:
Deposit Phase: A phase where users deposit their funds to top up the Elusiv account balance privately.
Logic Phase: Where Elusiv Computes a hash based on the amount of user deposit, type of user deposit, and a secret value called nullified. A string is generated from the hash value of the above three parameters. This string is called a commitment. Once the logic phase is done the Nullifier is given to the user and recorded on-chain to prevent double-spending and make sure a commitment is valid only once.
Claim Phase: Where a user wants to use the balance in the account to send the money to another wallet address, they need to complete a ZKP to verify that they know the value of the Nullifier to complete the process, this allows the user to spend the commitment they’ve previously made by depositing the tokens.
What does Elusiv offer to empower Privacy?
In this section let us go through the extensive feature set being offered by Elusiv to empower the privacy layer of the web3 ecosystem.
Encrypted and Private Transactions

Elusiv allows users to encrypt every step of the payment process to stay completely private and prevent any backtracking of payments processed via the Elusiv platform.
The first step of the payment process would be depositing funds into the wallet. Elusiv allows users to top up their private balance with SOL or any other SPL-Token, including the most popular USDC and USDT stablecoins. This allows users to maintain their wallets with stable sources of worth using the stablecoins on Solana.
The next step in the payment process would be the transaction itself, and Elusiv offers a completely private transaction experience, where the user transfers the tokens to the Elusiv pool as discussed in the technical architecture of Elusiv, and the Elusiv platform relays these tokens to the receiver, thus delinking the sender and receiver from the transaction details, thus preventing any backtracking or pinpointing of the identity of the sender or receiver of tokens.
And the final step in the payment process would be the ability to prove that the transaction happened correctly to someone selectively. This can be done by generating the required viewing keys and sharing them with authorized parties.
Gated Privacy
Users need privacy from the public and the community in general who can build data mining models to trace back the sender and receiver which risks the privacy of the transaction. But Elusiv provides a gated privacy model along with the standard complete privacy approach. This gated privacy model allows users to share the transaction details with a TTP (Trusted Third Party), and this gated privacy model consists of two important components:
Spending Key: This key is similar to the private key of your crypto wallet, one who controls the spending key can spend the assets topped up in your Elusiv account. Hence users must never share their spending key with someone.
Root Viewing Key: This is a read only key where users can share this key to other Trusted Third Parties like Tax agencies, and Authorities if asked. This gives them the access to read all the transaction details performed by a wallet on Elusiv.
Warden Network

Warden Network consists of units called “Wardens”, which patrol the network to maintain the integrity, compliance, and decentralization of the Elusiv platform.
Another key role the Warden network fulfills is that it relays the requests and responses between the Elusiv Client and the Blockchain, these requests and responses include user fund deposits, fund withdrawals, etc.
Also as we discussed the drawbacks of an application like Tornado Cash, and Warden Netowork prevents this, by blocking Malicious Actors thus preventing interactions between Bad actors and Regular users on the network.
Privacy 🤝 Compliance = Decentralized Compliance
Elusiv maintains the integrity of the platform by building a series of steps and measures to embrace Decentralized Compliance, rather than taking the easy way of embedding a KYC form for the users. KYC is a great way to verify users but it gives away too much about the user to the platform. Thus Decentralized Compliance is the perfect way to maintain the high privacy standards set by Elusiv. These measures include:
Gated Privacy and Viewing Keys for TTP: As discussed above these viewing keys allows users to verify their integrity in case any federal or tax authorities question them, by giving the viewer access to the transactions they performed.
Autonomous Protocol Analysis (APA) and Warden Network: APA is a background tool that runs on top of the Elusiv platform and the Warden network to prevent interactions between regular users and Malicious actors by constantly updating the community-driven blocklist of bad actors in the network.
DEV Delight: Elusiv Web3 SDK
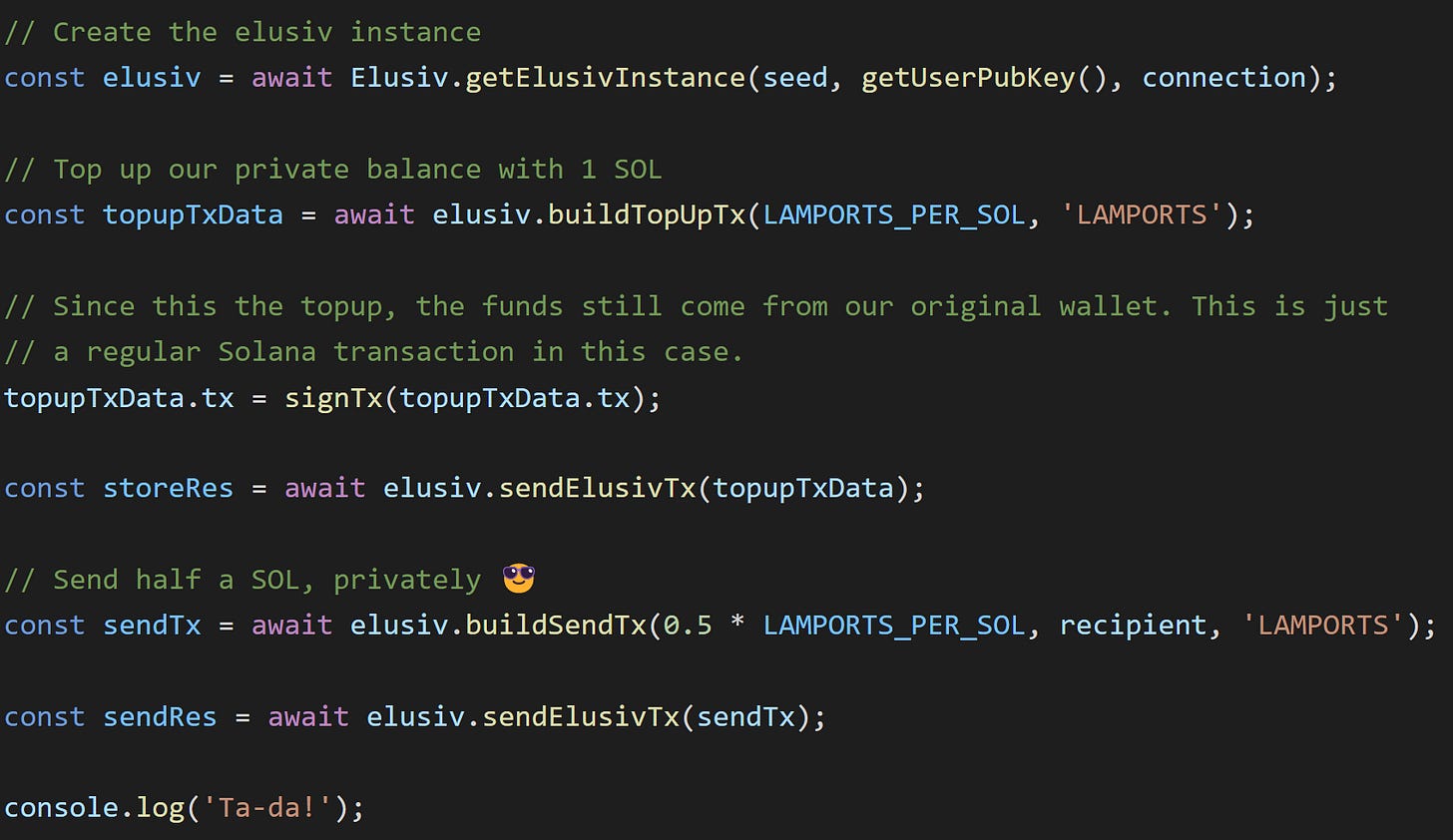
Elusiv as a platform is trying to maintain the transparency of the application by embracing open-source standards. They made their Elusiv Typescript SDK open-sourced for developers to build on top of Elusiv’s amazing privacy layer. This allows other privacy focussed applications to make their presence in the web3 Ecosystem without reinventing the wheel of technology! Here’s a look at a simple use case of this amazing Typescript SDK:
Yes, you guessed it right, Elusiv just didn’t stop there for the devs, they made their complete platform’s Source code, open-sourced, check that out, contribute, and build on top of it:
Elusiv VM’s
Elusiv VMs are an exciting piece of tech being built by the Elusiv team for the future, when released, it enables other services to integrate the privacy layer built by Elusiv into their applications with ease. This helps someone use these ZK-based privacy solutions in their applications without the knowledge of advanced cryptography.
Potential Use Cases of Elusiv’s Technology
Elusiv’s technology has a vast range of use cases with the currently implemented features and let us explore some of them in this section, to understand the impact of this project in the real-time web3 user experience and the way it empowers the ecosystem.
Elusiv acts as a universal encryption layer on web3 to encrypt transactions, as we know in web3 these transactions can range a wide array of use cases from financial or DeFi transactions to social network transactions on web3, gaming, etc, let us see some of the potential, untapped use cases of Elusiv’s generalized web3 encryption standard:
Financial Transactions: Elusiv’s technology can be used in regular on-chain transactions as we discussed all the way from the beginning, also it can be used to prevent eyes in the market to catch up on the movements of whales, to predict the market and thus making it unstable with a single user’s movement.
Anonymous Voting: Elusiv’s technology can be extended to DAOs to implement anonymous voting by encrypting each transaction in the polling process, thus eliminating the chance of influence of votes on others, leading to a fair polling process.
Legal Transactions: A zero-knowledge proof private transaction platform like Elusiv can be used to securely and anonymously conduct legal transactions such as property transfers, wills, and trusts. This would help to ensure privacy and security in the transfer of legal assets.
Gaming: Elusiv being a secure ZK-Privacy platform, can be used to securely and anonymously conduct transactions in online gaming. This would help to prevent fraud and ensure that players are treated fairly.
Identity Verification: Elusiv can be used to verify the identity of individuals without the need for sharing personal information. This would help to protect personal privacy while still ensuring security.
Integrations and Elusiv’s Competitive Landscape
Elusiv storming into the privacy layer scene of Solana recently made some good frens with some of the best developer communities and platforms out there:

Monstre is a platform that recently integrated the Elusiv SDK into its platform. Being a payment platform that allows users to transact NFT gift cards, Elusiv is a perfect fit for users on Monstre to spend their gift cards privately.
Also, Elusiv partnered with Solana Pay to allow sharing tokens privately using the trusted Solana Pay on-chain payment standard.
Elusiv’s biggest competitor in the Solana ecosystem is Light Protocol, which is aiming to build on a similar vision, a ZK privacy layer on Solana.

But Elusiv is uniquely positioned in the space with some major advantages that other competitors are not focussing on or not cracked them yet, they are:
1. Decentralized compliance
2. SDK
3. SPL token support
4. Integration with the Solana Pay standard
These special features give Elusiv a headstart while the Solana ecosystem is going mainstream to bring more users to the web3 ecosystem in the near future!
Beginners guide on how to use Elusiv:
The first step would be to connect your favorite Solana wallet to top up your Elusiv account:

Choose from the list of supported SPL tokens and fill in the sender’s wallet address to send the tokens:

Check out the Explorer tab to verify the history of your transactions.
Check out the compliance explorer to check the interactions of your transactions, and verify if they are not flagged or blocked by the APA and Elusiv’s warden network.

My Thoughts and Conclusion
Private transactions are going to be a big thing for web3 once the threshold of mainstream adoption is breached. And Elusiv is building the privacy infrastructure for future users to welcome them into the web3 ecosystem with all the required privacy-preserving features to maintain the integrity and standards of web3 ideals.
The best thing I loved about Elusiv is their ingenious solution on how they used the existing zkSNARKS technology to extend the idea to something so important to the web3 ecosystem, also the way they open-sourced the complete platform for the future developers is greatly commendable.
Thank you for giving this long technical deep dive a read. Hope I made it a fun and interesting experience for you all, if you liked the article give a like, share it with your friends, and give your feedback as a comment below!
💌
Regards,
Rohit Kumar Varma
References:
Elusiv website: https://elusiv.io/
Elusiv Docs: https://docs.elusiv.io/
Elusiv’s App: https://app.elusiv.io/
Elusiv’s SDK: https://elusiv-privacy.github.io/elusiv-sdk/
Elusiv’s Github: https://github.com/elusiv-privacy
Elusiv Twitter: https://twitter.com/elusivprivacy
Light Protocol: https://www.lightprotocol.com